How a single space killed my detections
UPDATE 16/7/2024 – Identified a pattern where the affected commands are “external” commands to cmd.exe, as in, they are actual executables themselves. Ipconfig, net, arp and ping each trigger an external executable, and somewhere in that process the extra space is being added. Internal commands can be found by writing “help” inside of cmd.
It all began on a quiet Thursday evening. I was sitting down with a friend, walking them through the process of creating rules for the SIEM system we both worked with. We decided to start with a simple rule, using the SIGMA framework, and chose a command that could be easily tested: “ipconfig /all.”
Excited to see our work in action, I ran the command on my virtual machine and waited for the logs to arrive in the SIEM. Minutes passed, and nothing happened. Our rule didn’t fire. We double-checked everything, puzzled and frustrated. What could have gone wrong?
For half an hour, we were stumped. Then, a realization struck me: the rule hadn’t triggered because the “commandLine” included two spaces between “ipconfig” and “/all.” This tiny, almost invisible detail was enough to throw everything off. And it wasn’t just “ipconfig” – commands like “ping,” “net,” and “arp” were also affected. To make things even more perplexing, running the same commands from PowerShell produced only one space, suggesting the issue lay somewhere within cmd.exe.
What on earth was going on? Intrigued and a bit dismayed, I turned to the wider cybersecurity community. I sent out messages on Twitter to experts and researchers I follow. Their responses were surprising: this issue had been known for years.
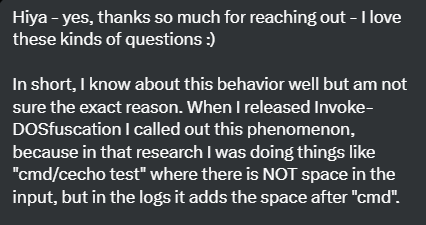
@nas_bench, link to the Twitter post
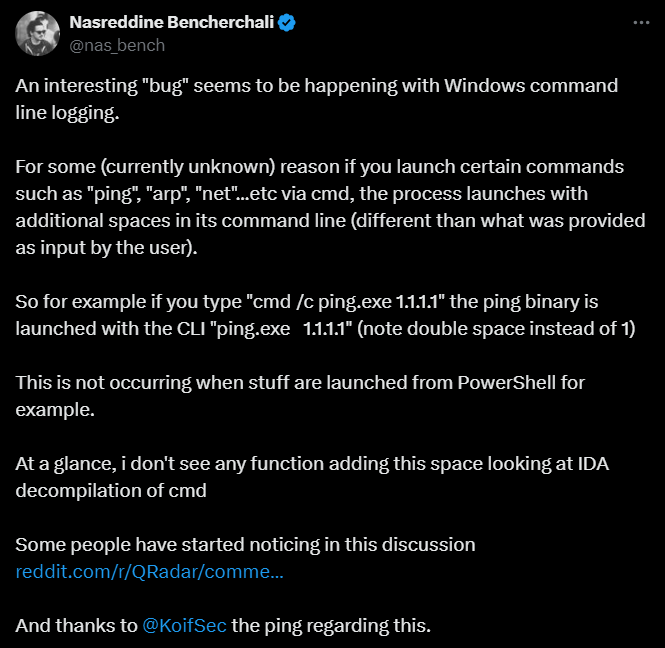
After taking a deeper look at the Windows logs in the event viewer, we managed to see that the XML payload itself does NOT include two spaces, but only one, as it should. Still, the logs arrive at the SIEM with TWO spaces (tested on Splunk and QRadar):
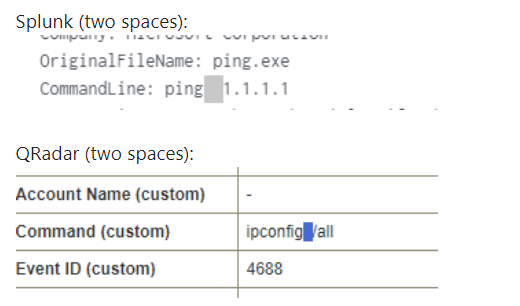
@Hexacorn suggests the following:
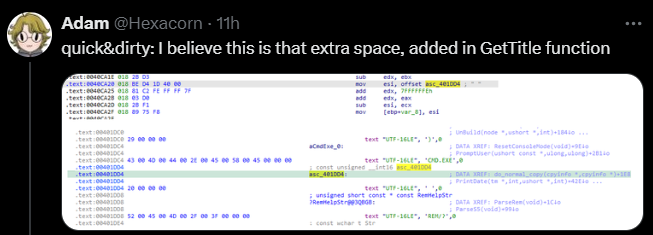
However, this is still just a theory. We still don’t know the confirmed root cause for this.
So, what does this mean for anyone using rules from the SIGMA repository that rely on these commands? Simply put, you might be missing true positives. I highly recommend reviewing and tuning your rules to account for this two-space bug.
As we await further findings, this strange saga of spaces serves as a reminder of how even the smallest details can have big impacts in the world of cybersecurity. I will update this post whenever I get new information!
